Snitching On Apps That Snitch On You
Kyle Rankin
President
Purism
Introduction
- Phones are our most personal computers
- Most vulnerable to privacy abuses
- Android/iOS hide app snitching
- Hide OS snitching even more
- Growing problem on desktop OSes
- Less of a problem on Linux
- To catch snitches, audit network traffic
- OpenSnitch a desktop-friendly tool for Linux
- Not just snitching, malicious activity.
This talk:
- Your phone snitches on you
- Your desktop snitches on you
- Firewalls for desktop OSes
- What is OpenSnitch
- How to install
- Training and using
- Future plans
Your phone snitches on you
Your desktop snitches on you
Firewalls for desktop OSes
- Traditionally firewalls designed for servers
- Focus is services listening on ports, blocking incoming traffic
- Default desktops have no public listening services
- Better focus for desktops is outgoing traffic
- Catch apps that phone home, apps that shouldn't need network
- Catch malicious software
- Block traffic based on app, remote connection details
- Should fail safe, deny by default.
What is OpenSnitch
- OpenSnitch application firewall for Linux based on MacOS "Little Snitch"
- Has service that connects to kernel, monitors outbound traffic
- Uses nftables/iptables to create firewall rules
- Provides UI to manage rules, see events
- UI pops up for new outbound connections w/o rules
- Connection temporarily blocked if no response in time
- Rules can expire or be permanent
- Allows fine-grained rules.
How to install
- Not in all distros, easiest install from GH release repo
- Provides deb/rpm, built for x86 and ARM
- Install opensnitch service + python UI package.
Training and using
UI
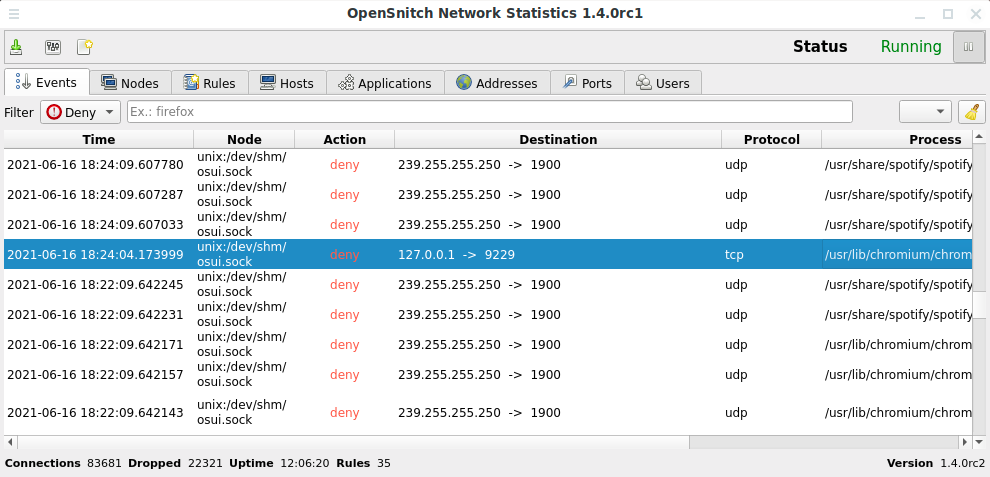
Training and using
Adaptive UI
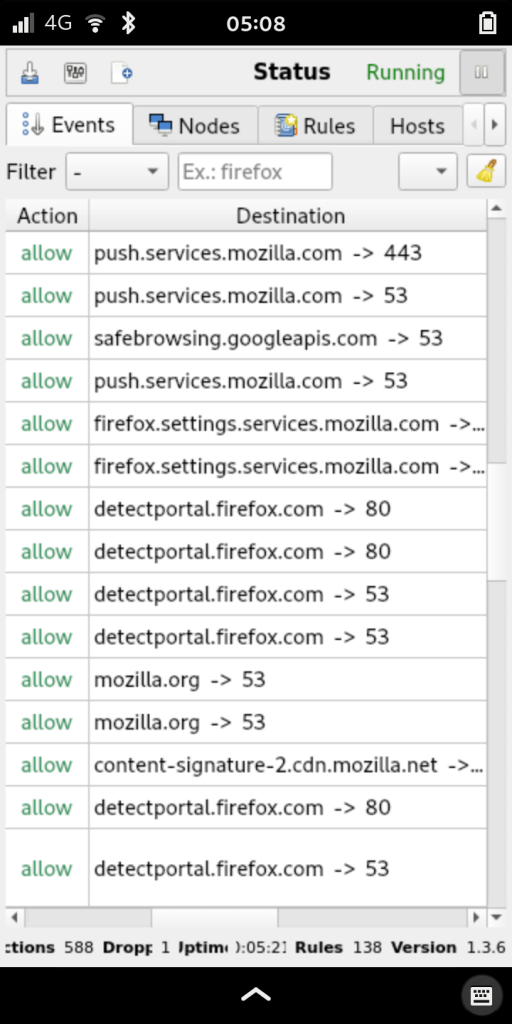
Training and using
Rules
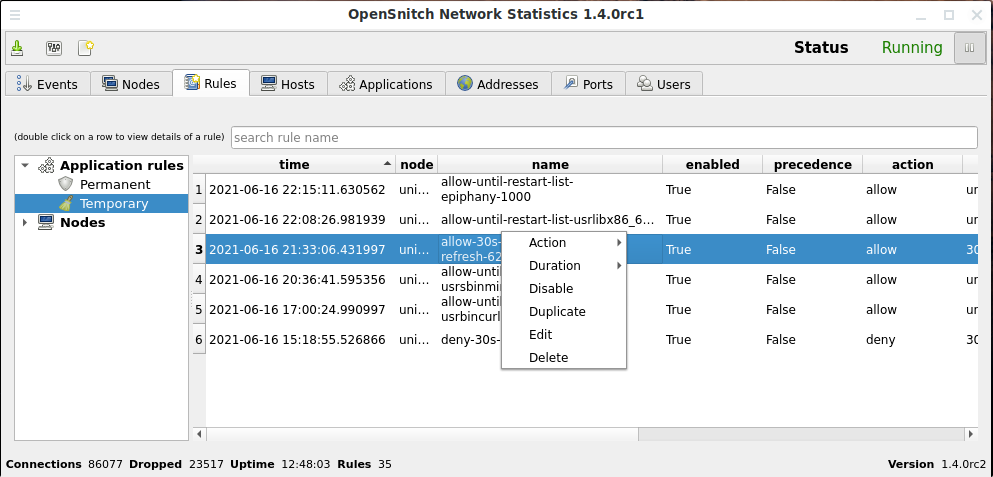
Training and using
Warning window
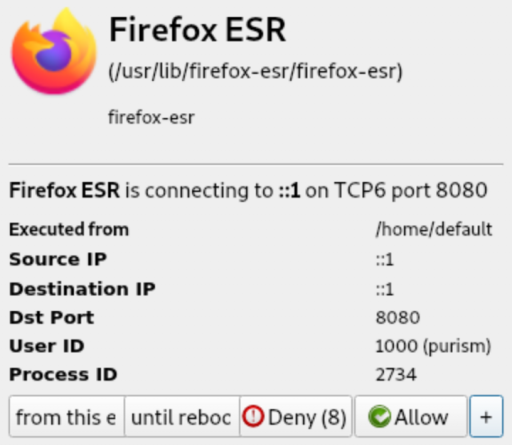
Training and using
Warning window expanded
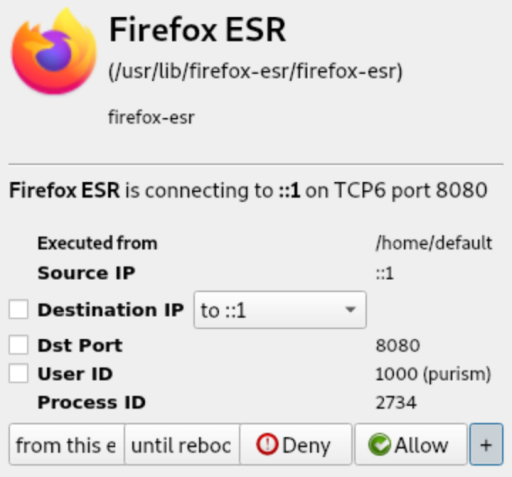
Training and using
Training tips
- Not necessarily for beginners
- Takes a week or two to train
- Pop-ups can be distracting at first
- Increase default timeout to 25s
- Change default duration to 15m
- Start with frequent apps
- When in doubt, deny for 15m
- Set Events tab to filter for blocked traffic
- Can also tweak rules directly in Rules tab.
Future Plans
- Working to package in PureOS
- Not running by default until ease-of-use improves
- Collect reasonable default rules into optional package
- Possibly groups of rules (relaxed/medium/strict).
Questions?
Additional Resources




